The Chinese government’s intrusions into America’s telecommunications and other critical infrastructure networks this year appears to signal a shift from cyberspying as usual to prepping for destructive attacks.
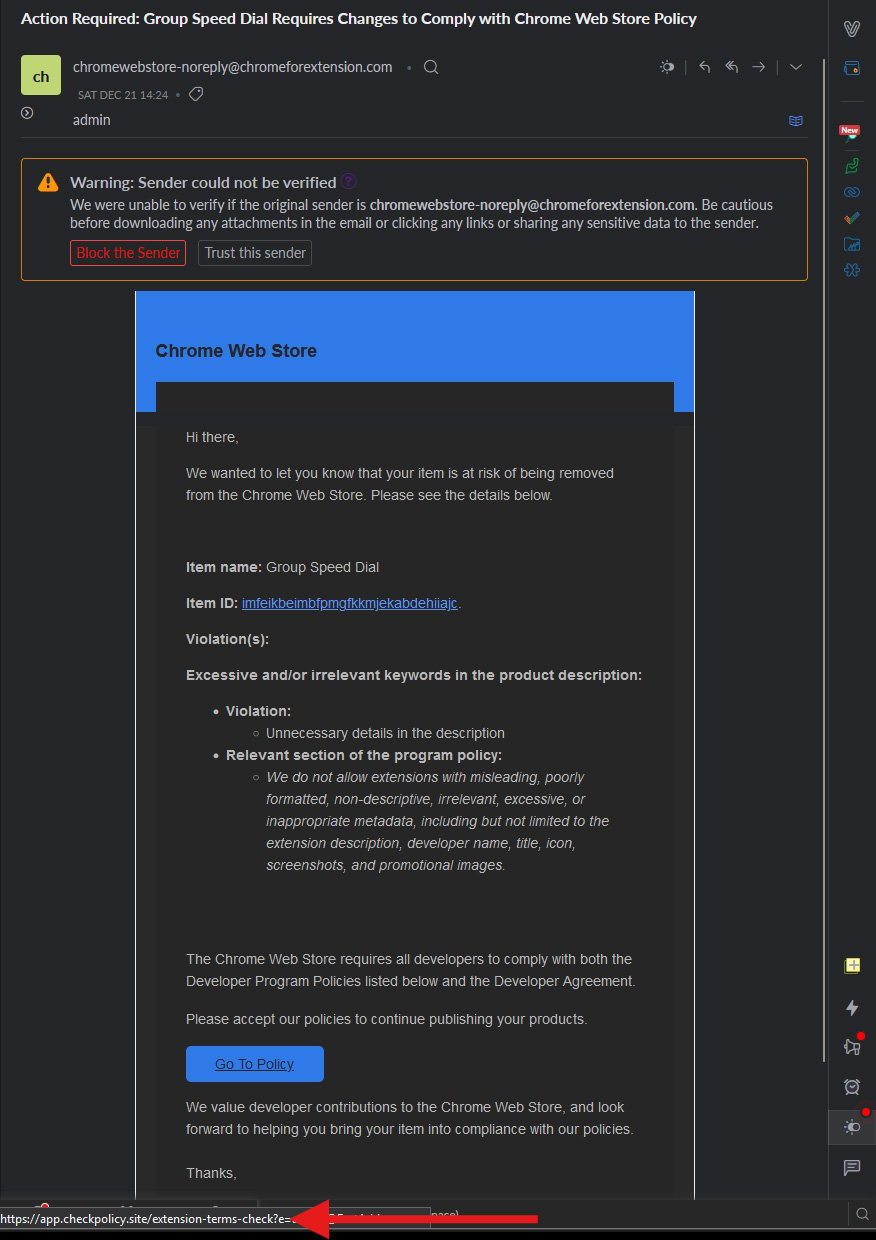
The FBI and other US federal agencies rang in 2024 boasting about disrupting a Chinese botnet composed of “hundreds” of outdated routers intent on breaking into US critical infrastructure facilities. Spoiler alert: the botnet is back.
This same government-backed crew also compromised at least one large US city’s emergency services network, and has been conducting reconnaissance and enumeration of “multiple” American electric companies since early 2023.
Soon after these intrusions came to light, the Feds began issuing very public alerts that Volt Typhoon was preparing to “wreak havoc” on American infrastructure and “cause societal chaos” in the US.
“Volt Typhoon’s choice of targets and pattern of behavior is not consistent with traditional cyber espionage or intelligence gathering operations, and the US authoring agencies assess with high confidence that Volt Typhoon actors are pre-positioning themselves on IT networks to enable lateral movement to OT assets to disrupt functions,” the government agencies warned.
The public learned later in the year that another Beijing hacking unit, this one called Salt Typhoon, had broken into American telecommunications networks in what one senior US senator called the “worst telecom hack in our nation’s history – by far.”
According to government and infosec sources, the attacks remain ongoing.
“We cannot say with certainty that the adversary has been evicted, because we still don’t know the scope of what they’re doing,” Jeff Greene, CISA’s executive assistant director for cybersecurity, told reporters during a Salt Typhoon briefing in early December.
‘Every org should be put on notice’
“Every organization should look at this as being put on notice that there are hostile nation state entities,” CrowdStrike Senior VP of Counter Adversary Operations Adam Meyers told The Register. “If you are involved in any degree of business that ties into the broader international ecosystem, or you’re providing services that are of logistical importance for critical infrastructure, you’re in the line of fire.”
CrowdStrike tracks 63 different China-linked groups, and about two dozen of these are currently active, according to Meyers. In November, Meyers testified before a Senate committee on how the cyberthreats from the Middle Kingdom have evolved over the past two decades.
Prior to 2015, these tended to be “smash-and-grab” raids, he said, noting that over the years, they have become more targeted intrusions that focus on high-value individuals and information: sources of political and military secrets, and intellectual property that can advance China’s national interests.
Even more worrisome is that at least one of these state-sponsored groups, Volt Typhoon, which CrowdStrike tracks as “Vanguard Panda,” appears to be pre-positioning deep inside American critical infrastructure networks so it’s ready for disruptive or destructive attacks preceding or coinciding with military activities.
“The reason that Vanguard Panda attracted so much attention was that it was the first time that there was a demonstrable aspect of pre-positioning,” Meyers said during an interview. “This would be like if the Russians, back in the ’60s, thought they were going to invade the United States. Their pre-positioning would be to hide caches of weapons and resources that they could access as they mounted their invasion across the US.”
This would be like if the Russians, back in the ’60s, were going to invade. Their pre-positioning would be to hide caches of weapons they could access as they mounted their invasion across the US
Plus, it’s unlikely that blowing up the botnet earlier this year did anything to disrupt the larger organization, or its future plans, he added.
“Disrupting that did not impact Vanguard Panda,” Meyers said. “It did not impact their ability to access the targets that they had gained access to and were continuing to maintain persistence.”
He said he’s doubtful that Volt Typhoon/Vanguard Panda was even running the botnet infrastructure. “That was likely another group that was tasked with providing communications infrastructure, and when that got disrupted, you would have to expect that there would have been a secondary path that would have been on standby,” Meyers noted. “They’re not going to just leave things to chance. If there’s a primary mechanism that they’re using, then they want a secondary and a tertiary one.”
Before implanting the KV botnet malware on routers and other devices, Volt Typhoon has to break in, which usually involved exploiting bugs in firewalls, VPN appliances, and web servers, or abusing misconfigurations or weak – sometimes non-existent – passwords in these products.
Volt Typhoon’s post-exploitation activity
Tenable last month published a list of some of the CVEs that the crew has exploited in the past to gain initial access. These include a vulnerability in the web management interface of FatPipe WARP, IPVPN, and MPVPN software that allows a remote, unauthenticated attacker to upload a file to any location on the filesystem (CVE-2021-27860), a critical authentication bypass flaw in Zoho ManageEngine ADSelfService Plus (CVE-2021-40539), two critical heap-based buffer overflow bugs in Fortinet FortiOS and FortiProxy (CVE-2022-42475 and CVE-2023-27997) and a file upload flaw in Versa Director SD-WAN (CVE-2024-39717).
Lumen Technologies’ Black Lotus Labs in August warned that Volt Typhoon was abusing the Versa vulnerability CVE-2024-39717 to plant custom, credential-harvesting web shells on customers’ networks and noted that these attacks are “likely ongoing” against unpatched systems.
“What’s unique about Volt Typhoon is the post-exploitation activity,” Tenable research engineer Scott Caveza told The Register. It doesn’t use custom malware, which can be more easily spotted by antivirus software, but instead uses legitimate software products and credentials to snoop around and avoid detection.
These include Windows tools (cmd.exe, netsh, and PowerShell) for command execution and lateral movement, Mimikatz to extract credentials from memory, Remote Desktop Protocol (RDP) to burrow deeper into internal systems, and Windows Task Scheduler to establish scheduled tasks for regular, persistent access.
“Just executing normal commands and binaries that would be found on a Windows system to do reconnaissance, and further their way through the network,” Caveza said. “It’s very stealth activity, and really speaks to the skill this group has at evading security software suites and making the traffic look seemingly normal.”
In addition to Volt Typhoon and some of the other Chinese government groups using stealthy, so-called “living-off-the-land” techniques, another noteworthy aspect of their ongoing operations targeting critical industries is the US government’s very loud response to the attacks.
Caught in the cookie jar
Not only did the FBI, CISA, and other government agencies sound the alarm on the Chinese intruders, but they also published a threat hunting guide and listed actions to mitigate Volt Typhoon activity, including patching internet-facing systems, using phishing-resistant multi-factor authentication, and ditching outdated gear that is no longer supported by the manufacturer.
“Number one, kudos to our government,” ZeroFox VP of Intelligence Adam Darrah told The Register. “I do applaud the United States government for being more bold in publicizing these campaigns and saying here’s how to prevent this being an issue. It’s a way to crowdsource national defense.”
While every major intelligence agency in the world spies on adversarial – and sometimes even friendly – government, China’s cyberoperations this year should be a “wake-up call” to people, Darrah added.
“China has historically been very careful and good about not getting publicly caught with their hand in the American military cookie jar,” he said. “So what was interesting to me: Number one they got caught. Number two: it was publicized. And number three: I’m happy to see this, because it’s time to stop pretending China is this peaceful country that only wants to steal our IP for economic and trade reasons. That’s not true.”
Rafe Pilling, director of threat intelligence for the Secureworks counter threat unit, also highlighted the US government’s efforts to encourage people to mitigate the threat posed by Volt Typhoon. And now only “the threat that has been posed today” with the targeted reconnaissance and espionage activities, “but perhaps more about the threat posed in the future – the wider, unknown activity that might be out there.”
“This includes the pre-positioning warnings and readying for future attacks.”
Piling’s team covers the gamut of threat groups, from financially motivated cybercrime organizations to nation-state attackers, and China “consistently tops our list of state sponsored actors,” he told The Register.
The first cases that Securworks now attributes to Volt Typhoon (it tracks this crew as Bronze Silhouette) occurred in June and September 2021.
But at the time, “we had a number of incidents we responded to for customers involving that threat group that we just had a question mark over,” Piling said. “They didn’t fall into any of the other buckets we tracked, so we out a question mark, ‘China?’ over those incidents.”
It was only years later, after information sharing efforts with public and private researchers, “that you see there is this wider set of activities targeting organizations in mainland United States all the way out to telcos in Guam,” he added.
But even back in 2021, “the activity we saw certainly looked like access-type operations,” Piling said. “Once you get past the access stage, you can achieve a number of intents, everything from espionage to pre-positioning for disruptive operations. And they’re not mutually exclusive.”
While security and incident response firms get called in after an attack has occurred, the defenders on the front lines are those working in the water, electric grid, oil and gas, and other critical sectors.
Front-line defenders
These are among operational technology (OT) security Xona Systems’ customers, and the consensus is: “There’s a lot more that could be done to protect critical infrastructure,” COO Bill Cantrell told The Register. “The overriding theme is that there’s just not enough funding.”
The biggest concern among critical infrastructure owners and operators continues to be physical safety and reliability. “Those things have always been at the forefront in this industry, Cantrell said. “There’s a lot of very dangerous, high-power equipment and so it’s making sure it’s reliable, it’s safe, and there are good backup procedures.”
These are very real concerns. Critical systems providing drinking water or heat can’t fail without potential life-and-death consequences, and shutting down these systems to update or patch security flaws introduces a raft of physical-world risks.
Over the last several years, however, there have been added concerns around network connectivity and remote access as more OT and IoT devices and systems become connected to the internet.
“It’s a new vector of pressure that has been put on these OT folks,” Cantrell said. “It’s a world where the OT guys don’t understand the networking and cyber issues, and the IT guys don’t really understand all of the constraints around safety and reliability that go along with these OT networks.”
The most important thing that critical industries should be doing is to modernize secure access to remote infrastructure, according to Cantrell. “That’s where most of these breaches come from is through stolen credentials, VPNs, older jump boxes,” he said, adding that visibility is another key piece. “Half the time, they don’t even know everything that is on the network.”
And it’s a lot to deal with for an org using legacy OT gear and trying to get up to speed on IT concepts like zero-trust access while facing down attempted attacks from ransomware crews and nation-states on a daily basis.
“The scary thing is that some of these threats may be laying in wait and dormant right now,” Cantrell said. “They may be doing some intel collection and possibly laying in wait to trigger actions when they feel it’s necessary.”
He echoed CISA and the FBI’s alerts of late about it being incredibly hard to kick intruders off of critical networks when you don’t know they are there in the first place. “Some of them may be compromised, and they may not even know it.” ®